Credibility Crunch for Tech Companies Over Prism; People’s Locations Could Be Tracked
June 8, 2013 Leave a comment
Updated June 7, 2013, 7:51 p.m. ET
Credibility Crunch for Tech Companies Over Prism
By AMIR EFRATI, SHIRA OVIDE and EVELYN M. RUSLI
With Silicon Valley’s credibility in protecting consumer privacy on the line, many of the largest Web companies on Friday emphasized they aren’t giving the U.S. government a direct pipe into their networks as part of a secret program to monitor foreign nationals.
But the denials of involvement by Google Inc., GOOG +1.75% Microsoft Corp.MSFT +2.03% and others, which come at the same time the Obama administration confirmed the existence of such a program, raised questions about how data is ending up in the hands of the government.
The issues are especially acute for companies who make their business by collecting and processing customers’ most personal data and secrets.Google CEO Larry Page and Chief Legal Officer David Drummond said in a blog post that the company doesn’t give U.S. government investigators “open-ended access” to its network and hadn’t “joined” a program known as Prism and run by the National Security Agency.
The executives said Google only hands over data based on legally-authorized requests that it reviews individually.
U.S. officials briefed on the matter said Friday that the NSA receives copies of data through a system they set up with a court order. They don’t have direct access to the company computers, those people said.
Companies including Apple Inc., AAPL +0.76% Facebook Inc. FB +1.40% andYahoo Inc. YHOO +3.17% all specified in some way that the government doesn’t have “direct access” to their networks. But they didn’t say whether the government may be indirectly siphoning user information—including subject lines of emails and photos stored online—through an intermediary in response to secret court orders.
One former government official and cybersecurity legal expert said the companies are likely carefully parsing their words. This person said it is likely that the government is able to get copies of data in real-time or near real-time without accessing the Internet companies’ central servers.
The Internet companies didn’t answer questions about these potential side doors into their data.
Google and Microsoft release regular reports that outline the number of government requests for user data per year, but such reports don’t include the kind of court-ordered requests made by the NSA for its surveillance of foreign nationals. Such requests prohibit the recipients from disclosing them.
U.S. officials also shed little additional light on how the program works on Friday. The National Security Agency referred questions about Prism on Friday to the office of the Director of National Intelligence. Representatives for the office didn’t immediately respond to questions.
Federal law-enforcement agencies can issue data-disclosure orders to the tech companies under the FISA Amendments Act, a law that permits the government to obtain surveillance orders from a special court without warrants on specific people.
The orders compel companies to provide data, such as the content of emails, files and photos, stored online.
The technical mechanism through which the tech companies comply with foreign-surveillance orders is unclear.
One industry executive familiar with the handling of data requests from U.S. intelligence agencies said companies have set up ways to cope with the volume of data by automating parts of the process. This method would allow data to be funneled to intelligence agencies without the need for manual steps by company employees.
Agency personnel, this person said, are likely to have the capability to conduct informal searches through company data to help narrow searches associated with particular individuals and aid in crafting formal data requests.
Internet giants have been repeatedly accused of funneling information about their users to the U.S. and other governments.
Two years ago, Julian Assange, the editor in chief of Wikileaks, called Facebook an “appalling” spy machine during a media interview, adding that he believed the social network, Google and Yahoo had “built-in interfaces for U.S intelligence.”
In a comment at the time, a Facebook spokesman said, “There has never been a time we have been pressured to turn over data.”
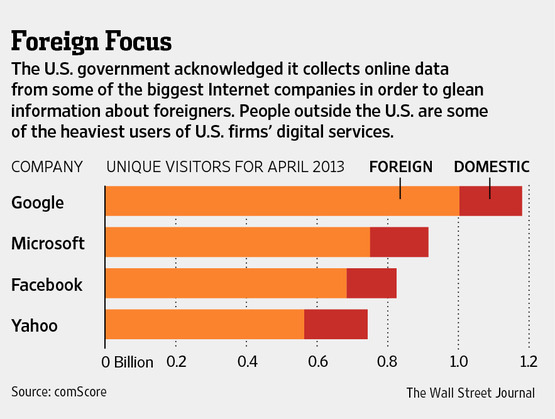
Obama administration officials stressed Friday that the NSA surveillance program focuses on foreign nationals, not Americans. But for companies like Facebook—which counts roughly 80% of its monthly users outside the U.S. and Canada—the disclosure of surveillance on foreign nationals raises its own problems.
A backlash, privacy advocates warned, may be particularly strong in Europe, where governments and citizens have been more sensitive to privacy issues.
Following the disclosure, some European lawmakers and regulators seized the opportunity to reiterate their commitment to protect privacy. German Justice Minister Sabine Leutheusser-Schnarrenberger told daily newspaper Die Welt that “German citizens don’t want their data to automatically end up with American authorities. It’s good and necessary for the U.S. to rethink its antiterror legislation.”
In the Middle East, where some governments have recently tried to restrict Internet access and use technology to crackdown on protesters, , the reaction was more muted. “I’m not shocked the U.S. has a very strong spy apparatus. I’m surprised they’re careless enough to let it come out,” said Wael Eskandar, an Egyptian blogger and activist.
The privacy questions also come at a time when Internet companies are trying to wedge themselves deeper into daily lives around the world. In Silicon Valley, data has become invaluable currency, to serve better ads, prod users to spend more time on services, and create a competitive advantage against rising upstarts.
“Here we are in the world of big data, and we know they can record every single thing,” said Michael Pachter, a Wedbush Securities analyst.
June 7, 2013, 6:49 p.m. ET
People’s Locations Could Be Tracked
Data collected by the National Security Agency’s program that monitors Americans’ phone calls could be used to track millions of people’s locations through their mobile devices at any given time, according to people familiar with cellphone systems.
This is part of a new reality of surveillance: Advances in technology have vastly expanded the types of data included in records of calls and other communications. So even if the content of a call or email message isn’t seen, governments are able to glean details about where people are, what they are doing and with whom they are communicating.
Supporters of the NSA program in Congress said Thursday that the monitoring is legal precisely because it doesn’t involve the content of communications but relies on this call-record information known as “metadata.”
“Our courts have consistently recognized that there is no reasonable expectation of privacy in this type of metadata information,” Senate Intelligence panel leaders Dianne Feinstein (D., Calif.) and Saxby Chambliss (R., Ga.) said Thursday. President Barack Obama called the NSA’s activities “modest encroachments” on privacy on Friday.
In a separate program, dubbed Prism, the NSA collects data that includes content, but that program targets Internet communications involving at least one foreign person, the White House confirmed on Thursday after reports in two newspapers.
Technical experts say metadata can be very revealing. This information can be “more revelatory than the content of calls,” said Susan Landau, a former Sun Microsystems Inc. engineer.
Take phone records of the sort described in a U.S. court order disclosed by the U.K.’s Guardian newspaper Wednesday.
Records from cellphone networks include an ID number of the nearest cell tower and often say which direction that tower is in, said Matt Blaze, a computer-science professor at the University of Pennsylvania and a former researcher at AT&T Labs.
That can provide “a pretty good idea” of where someone is, he said. In rural areas, this might be within a mile or more; in urban areas, where there are many cellphone towers, this area could be a few blocks. In places where small cellphone base stations are used to fill in holes in coverage, the location could even be narrowed to the floor of a building.
The court order to Verizon disclosed on Wednesday was not directed at the company’s wireless arm, and it didn’t include information on such cellphone tower or location data. But Mr. Blaze said that type of data is included automatically on call records held by wireless companies.
Mr. Blaze said the companies get this data anytime a person makes or receives a call, and anytime the person moves into coverage of a new tower. With smartphones, such transmissions also happen whenever the phone connects to transmit data.
In 2011, a German politician named Malte Spitz received six months of his own data from a German cellular provider after a legal battle. The nearly 36,000 records, when plotted out on a map, show his life in detail: taking trains, attending events in Berlin and, most frequently, simply moving through his city.
This can show “whether someone goes to church on Sunday” and “whether they’re having an affair,” Ms. Landau said.
Police frequently use such data to investigate crimes, tracking, for example, where people suspected in drug deals go and who they are with.
The Wall Street Journal also reported this past week that address data from emails is handed over by some Internet service providers and included in the NSA’s monitoring system.
That can be more intrusive than people think. It could show, for example, people in a political or activist group communicating. Or it could show top executives writing frantic emails before a deal or crisis.
“You don’t have to know anything about the content; you just have to know who is making the call” to draw these connections, Ms. Landau said.
In this way, the NSA is using the data to target possible terrorists, people familiar with the effort told the Journal.
Other data being gathered in the program includes information on websites visited, as well as credit-card purchases, the Journal reported.
Details about precisely how data is collected under the Prism program remain unclear. That program was reported by the Guardian and Washington Post this week. The newspapers said technology giants including Google Inc., GOOG +1.75%Facebook Inc. FB +1.40% and Microsoft Corp. MSFT +2.03% were involved. The White House didn’t elaborate on how such communications are identified or segregated from domestic traffic.
Updated June 7, 2013, 9:25 a.m. ET
U.S. Collects Vast Data Trove
NSA Monitoring Includes Three Major Phone Companies, as Well as Online Activity
By SIOBHAN GORMAN, EVAN PEREZ and JANET HOOK
WASHINGTON—The National Security Agency’s monitoring of Americans includes customer records from the three major phone networks as well as emails and Web searches, and the agency also has cataloged credit-card transactions, said people familiar with the agency’s activities.
Jerry Seib explains how the far-reaching data collection conducted by the U.S. government includes phone companies in addition to Verizon, plus Internet service providers and Apple. Photo: Getty Images
The disclosure this week of an order by a secret U.S. court for Verizon Communications Inc.’s VZ +0.54%phone records set off the latest public discussion of the program. But people familiar with the NSA’s operations said the initiative also encompasses phone-call data from AT&T Inc. T -1.01% andSprint Nextel Corp., S -1.36% records from Internet-service providers and purchase information from credit-card providers.
The Obama administration says its review of complete phone records of U.S. citizens is a “necessary tool” in protecting the nation from terror threats. Is this the accepted new normal, or has the Obama administration pushed the bounds of civil liberties? Cato Institute Director of Information Policy Studies Jim Harper weighs in. Photo: Getty Images.
The agency is using its secret access to the communications of millions of Americans to target possible terrorists, said people familiar with the effort.
The NSA’s efforts have become institutionalized—yet not so well known to the public—under laws passed in the wake of the Sept. 11, 2001, attacks. Most members of Congress defended them Thursday as a way to root out terrorism, but civil-liberties groups decried the program.
“Everyone should just calm down and understand this isn’t anything that is brand new,” said Senate Majority LeaderHarry Reid (D., Nev.), who added that the phone-data program has “worked to prevent” terrorist attacks.
Senate Intelligence Chairman Dianne Feinstein (D., Calif.) said the program is lawful and that it must be renewed by the secret U.S. court every three months. She said the revelation about Verizon, reported by the London-based newspaper the Guardian, seemed to coincide with its latest renewal.
Civil-liberties advocates slammed the NSA’s actions. “The most recent surveillance program is breathtaking. It shows absolutely no effort to narrow or tailor the surveillance of citizens,” said Jonathan Turley, a constitutional law expert at George Washington University.
Meanwhile, the Obama administration acknowledged Thursday a secret NSA program dubbed Prism, which a senior administration official said targets only foreigners and was authorized under U.S. surveillance law. The Washington Post and the Guardian reported earlier Thursday the existence of the previously undisclosed program, which was described as providing the NSA and FBI direct access to server systems operated by tech companies that includeGoogle Inc., GOOG +1.75% Apple Inc.,AAPL +0.76% Facebook Inc.,FB +1.40% Yahoo Inc., YHOO +3.17%Microsoft Corp. MSFT +2.03% and Skype. The newspapers, citing what they said was an internal NSA document, said the agencies received the contents of emails, file transfers and live chats of the companies’ customers as part of their surveillance activities of foreigners whose activity online is routed through the U.S. The companies mentioned denied knowledge or participation in the program.
The arrangement with Verizon, AT&T and Sprint, the country’s three largest phone companies means, that every time the majority of Americans makes a call, NSA gets a record of the location, the number called, the time of the call and the length of the conversation, according to people familiar with the matter. The practice, which evolved out of warrantless wiretapping programs begun after 2001, is now approved by all three branches of the U.S. government.
AT&T has 107.3 million wireless customers and 31.2 million landline customers. Verizon has 98.9 million wireless customers and 22.2 million landline customers while Sprint has 55 million customers in total.
NSA also obtains access to data from Internet service providers on Internet use such as data about email or website visits, several former officials said. NSA has established similar relationships with credit-card companies, three former officials said.
It couldn’t be determined if any of the Internet or credit-card arrangements are ongoing, as are the phone company efforts, or one-shot collection efforts. The credit-card firms, phone companies and NSA declined to comment for this article.
Though extensive, the data collection effort doesn’t entail monitoring the content of emails or what is said in phone calls, said people familiar with the matter. Investigators gain access to so-called metadata, telling them who is communicating, through what medium, when, and where they are located.
But the disconnect between the program’s supporters and detractors underscored the difficulty Congress has had navigating new technology, national security and privacy.
The Obama administration, which inherited and embraced the program from the George W. Bush administration, moved Thursday to forcefully defend it. White House spokesman Josh Earnest called it “a critical tool in protecting the nation from terror threats.”
But Sen. Ron Wyden (D., Ore.), said he has warned about the breadth of the program for years, but only obliquely because of classification restrictions.
“When law-abiding Americans call their friends, who they call, when they call, and where they call from is private information,” he said. “Collecting this data about every single phone call that every American makes every day would be a massive invasion of Americans’ privacy.”
In the wake of the Sept. 11 attacks, phone records were collected without a court order as a component of the Bush-era warrantless surveillance program authorized by the 2001 USA Patriot Act, which permitted the collection of business records, former officials said.
The ad hoc nature of the NSA program changed after the Bush administration came under criticism for its handling of a separate, warrantless NSA eavesdropping program.
President Bush acknowledged its existence in late 2005, calling it the Terrorist Surveillance Program, or TSP.
When Democrats retook control of Congress in 2006, promising to investigate the administration’s counterterrorism policies, Bush administration officials moved to formalize court oversight of the NSA programs, according to former U.S. officials.
Congress in 2006 also made changes to the Patriot Act that made it easier for the government to collect phone-subscriber data under the Foreign Intelligence Surveillance Act.
Those changes helped the NSA collection program become institutionalized, rather than one conducted only under the authority of the president, said people familiar with the program.
Along with the TSP, the NSA collection of phone company customer data was put under the jurisdiction of a secret court that oversees the Foreign Intelligence Surveillance Act, according to officials.
David Kris, a former top national security lawyer at the Justice Department, told a congressional hearing in 2009 that the government first used the so-called business records authority in 2004.
At the time he was urging the reauthorization of the business-records provisions, known as Section 215 of the Patriot Act, which Congress later approved.
The phone records allow investigators to establish a database used to run queries when there is “reasonable, articulable suspicion” that the records are relevant and related to terrorist activity, Ms. Feinstein said Thursday.
Director of National Intelligence James Clapper also issued a defense of the phone data surveillance program, saying it is governed by a “robust legal regime.” Under the court order, the data can only “be queried when there is a reasonable suspicion, based on specific facts, that the particular basis for the query is associated with a foreign terrorist organization.” When the data is searched, all information acquired is “subject to strict restrictions on handling” overseen by the Justice Department and the surveillance court, and the program is reviewed roughly every 90 days, he said. Another U.S. official said less than 1% of the records are accessed.
The database allows investigators to “map” individuals connected with that information, said Jeremy Bash, who until recently was chief of staff at the Pentagon and is a former chief counsel to the House Intelligence committee.
“We are trying to find a needle in a haystack, and this is the haystack,” Mr. Bash said, referring to the database.
Sen. Wyden on Thursday questioned whether U.S. officials have been truthful in public descriptions of the program. In March, Mr. Wyden noted, he questioned Mr. Clapper, who said the NSA did not “wittingly” collect any type of data pertaining to millions Americans. Spokesmen for Mr. Clapper didn’t respond to requests for comment.
For civil libertarians, this week’s disclosure of the court authorization for part of the NSA program could offer new avenues for challenges. Federal courts largely have rebuffed efforts that target NSA surveillance programs, in part because no one could prove the information was being collected. The government, under both the Bush and Obama administrations, has successfully used its state-secrets privilege to block such lawsuits.
Jameel Jaffer, the American Civil Liberties Union’s deputy legal director, said the fact the FISA court record has now become public could give phone-company customers standing to bring a lawsuit.
“Now we have a set of people who can show they have been monitored,” he said.
Updated June 6, 2013, 11:32 p.m. ET
Tech Firms’ Data Is Also Tapped
By AMIR EFRATI, JESSICA E. LESSIN and JENNIFER VALENTINO-DEVRIES
The Obama administration acknowledged the existence Thursday of a secret National Security Agency program dubbed Prism, which a senior administration official said targets only foreigners and was authorized under U.S. surveillance law.
The existence of Prism was first revealed Thursday by the Guardian and Washington Post, which reported the NSA has been tapping a direct vein of consumer data fromApple Inc., AAPL +0.76% Google Inc., GOOG +1.75% Facebook Inc., FB +1.40%Microsoft Corp., MSFT +2.03% Yahoo Inc. YHOO +3.17% and other Internet companies, in some cases for years. The reports added to a suddenly renewed swirl of controversy of the Obama administration’s surveillance efforts, many of which have been in existence for years.
Many of the companies quickly denied they were involved, adding a note of confusion as to how the program might operate. The program’s revelation nonetheless could raise a long-simmering issue for tech companies whose very business depends on the collection and exchange of consumer data. The program is executed under a secret court order, and companies are compelled by law to comply.
Apple said it “has never heard” of the program. “We do not provide any government agency with direct access to our servers” it said in a statement.
Google implied it wasn’t aware of the program, saying in a statement it “does not have a ‘back door’ for the government to access private user data.”
A Microsoft spokeswoman said the company provides customer data only when it receives “a legally binding order or subpoena to do so.” She added, “If the government has a broader voluntary national security program to gather customer data we don’t participate in it.”
Facebook’s Chief Security Officer Joe Sullivan said in a statement the company does “not provide any government organization with direct access to Facebook servers.”
A Yahoo spokeswoman said in a statement, “We do not provide the government with direct access to our servers, systems, or network.”
In a written statement, Director of National Intelligence James Clapper emphasized the program’s foreign focus, saying it can’t be used to “intentionally target” Americans or anyone inside the U.S. Data collected under this program involves “extensive procedures, specifically approved by the court, to ensure that only non-U.S. persons outside the U.S. are targeted, and that minimize the acquisition, retention and dissemination of incidentally acquired information about U.S. persons.”
He denounced the disclosure of information about “this important and entirely legal program,” which he said “risks important protections for the security of Americans.”
The program is overseen by the Foreign Intelligence Surveillance Court, a secret national security court, as well as the executive branch and Congress. The administration official said it was recently reauthorized “after extensive hearings and debate” by Congress.
Civil-liberties advocates have long pointed out that technology firms typically allow blanket exceptions in their privacy policies for disclosure of customer data to governments.
“Most companies have weasel language or vague language that says that whatever other promises we made regarding privacy, we will still disclose information to the government under legal process” such as court orders, said Lee Tien, a senior staff attorney with the Electronic Frontier Foundation.
In the U.S., Google has fought back against “national security letters,” a tool used by the Federal Bureau of Investigation to seek people’s records without court approval. Google has several ongoing legal battles with the FBI surrounding its use of NSLs to try to compel the company to turn over personal information about its users, according to court records.
Google in recent years has also done more than any other Web company to disclose the scope of government requests for information about its users, privacy advocates say, including by publishing a biannual “transparency report” that breaks down the number of requests by country. Other big Web companies are now making similar disclosures.